Phishing: The Email Threat Lurking in Plain Sight
Today scams look official, feel personal, and are built to deceive. In fact, over 90% of successful cyberattacks start with a phishing email—often clicked on by well-meaning employees who never saw it coming.
Whether it’s a fake Microsoft alert, a spoofed CEO email, or a phony LinkedIn InMail, these scams are all about urgency, trust, and manipulation. If your team doesn’t know what to look for, your data, and your dollars are at risk.
So what’s the best defense? Awareness. And that starts with seeing what these phishing emails actually look like.
Five real phishing tactics that are actively hitting inboxes and fooling businesses
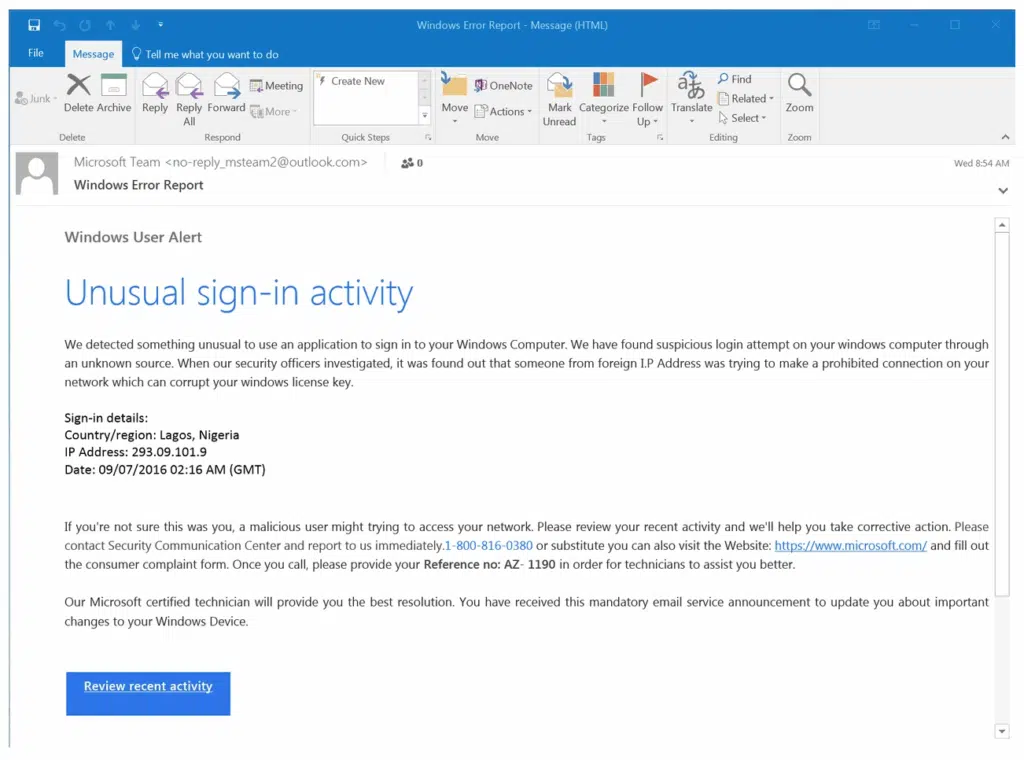
1. “Your Microsoft Account Has Been Locked” (Security Alert Scam)
Looks like:
- Official Microsoft branding
- Subject: “Unusual Sign-In Activity Detected”
- Button: “Secure My Account”
Red Flags:
- Slightly misspelled domain (e.g.,
micr0soft.com) - Hovering over links shows a shady URL
- Uses fear and urgency
Why it works: Employees see Microsoft and panic. They click before checking the sender.
2. “Invoice Attached” – With Malware Inside
Looks like:
- Email from a vendor or client
- Subject: “Invoice #785213 Ready”
- Attachment:
.htmlor Word doc with macros
Red Flags:
- Unexpected invoice or project name
- “Enable content” prompt when opened
- Generic greetings like “Dear Customer”
Why it works: We’re conditioned to open invoices—especially in finance roles.
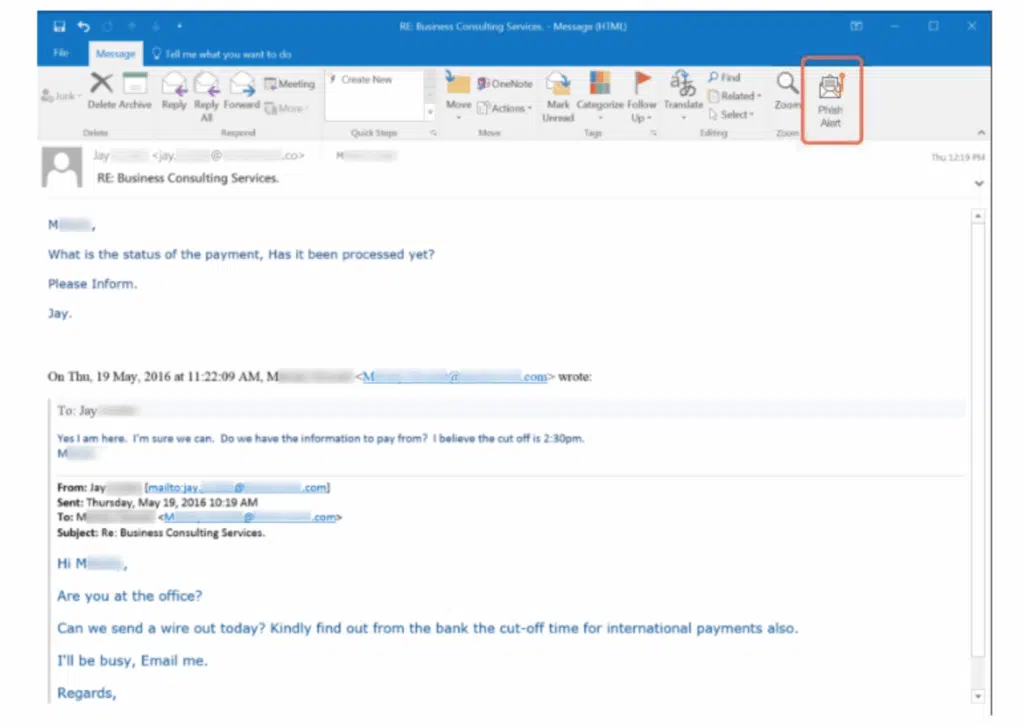
3. “Can You Do Me a Quick Favor?” (CEO Fraud/Business Email Compromise)
Looks like:
- Email from your CEO or manager
- Subject: “Need this handled ASAP”
Red Flags:
- Urges secrecy (“Don’t tell anyone”)
- Asks for gift cards or urgent payments
- Slight email spoofing (e.g.,
ceo@compaany.com)
Why it works: Employees want to help leadership and act quickly when asked.
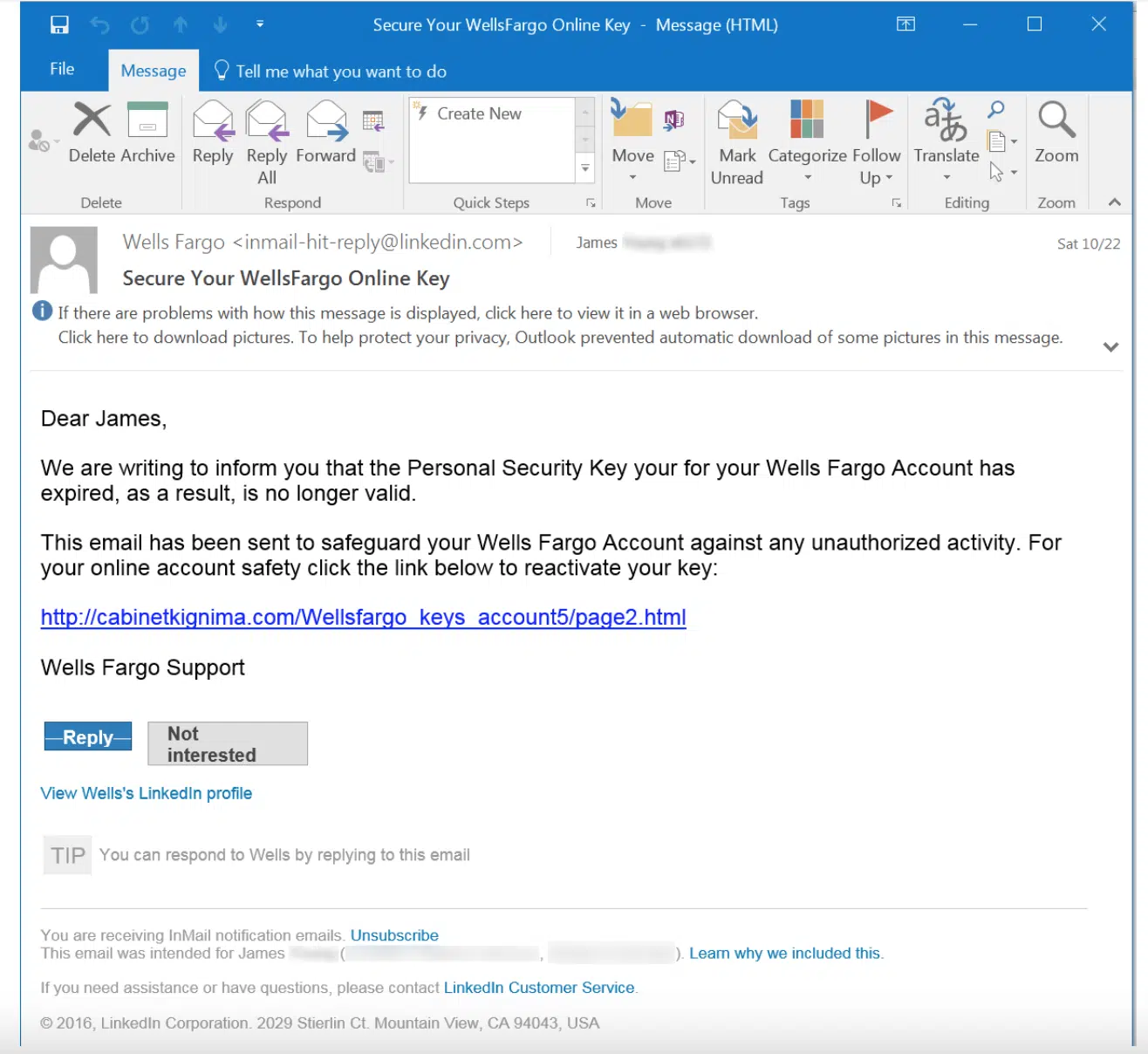
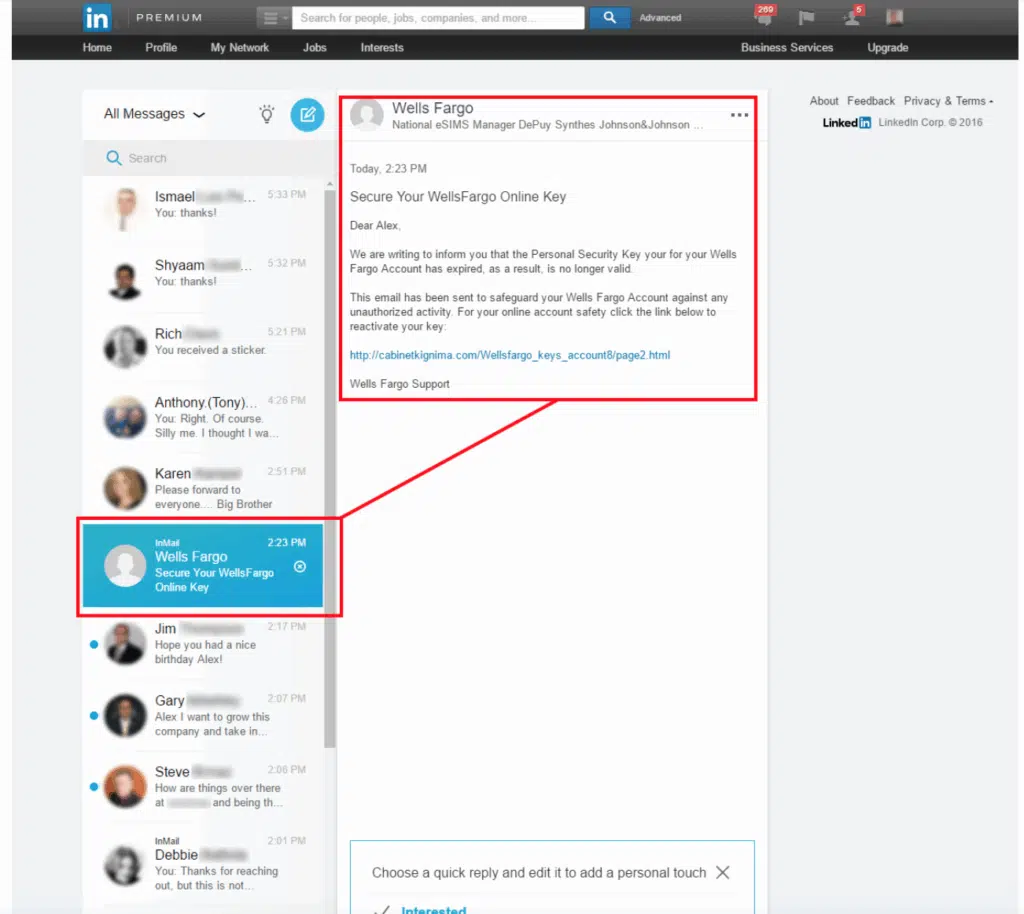
4. LinkedIn Phishing: The Spoofed InMail
Looks like:
- Message from a recruiter or colleague
- Subject: “You appeared in 7 searches this week”
- Link to fake login
Red Flags:
- Slight variations in LinkedIn’s domain
- Login page looks real—but URL is off
- No real InMail record on your actual LinkedIn account
Why it works: People trust LinkedIn as a professional platform and click without thinking.
5. Social Media Malware Spreaders
Looks like:
- “Hey is this you in this video?” messages
- Sent via Facebook, Instagram, or WhatsApp
- Leads to login prompt or malicious download
Red Flags:
- Out-of-character messages from friends
- Strange URLs or third-party video sites
- Requests re-login—capturing your credentials
Why it works: It preys on curiosity and friendship. Fast click, fast regret.
🚩 Top Red Flags to Train Your Team To Watch For
Even if the email looks legit, these signs scream phishing:
- Suspicious or misspelled sender addresses
- Unexpected attachments or links
- Requests for personal info, login credentials, or money
- A sense of urgency or pressure to act fast
- Generic greetings like “Dear user”
- Hovering over links shows mismatched or sketchy URLs
Why Smart People Still Fall for Phishing Emails
Think phishing only fools the clueless? Think again. Even tech-savvy, cautious folks can get duped because:
- The branding is perfect—logos, colors, and formatting are on point
- The sender looks familiar, sometimes even mimicking internal emails
- The tone feels natural—casual enough to feel real
- The message triggers panic or curiosity—two powerful emotions
That’s why training with visual examples is so effective. Once you’ve seen the tricks in action, you’ll be way harder to fool.
Train Your Team to Spot a Scam Before It’s Too Late
Don’t just send out an all-staff memo—make phishing awareness part of your culture. Here’s how to do it:
Easy Ways to Build Email Security Awareness:
- ✅ Download & Print Our Free Phishing Examples PDF
Share it in meetings or hang it in break rooms. - 🧑🏫 Run Quarterly “Phish Drills” or Simulations
See who clicks and who reports, then offer quick tips. - 📣 Discuss “Phishing of the Month”
Share a real example your company received. - 🖼️ Post Red Flag Posters in High-Traffic Areas
Especially near workstations. - 📩 Create a Simple Report Button or Email
Make it super easy for employees to flag sketchy emails.
Firewalls Can’t Catch Everything—People Can
Sure, spam filters and antivirus software help—but humans are still your strongest defense. Every click counts, and the damage from one bad link can ripple for months.
Training doesn’t have to be expensive or complicated. In fact, you can start today:
📄 [Download the Free Phishing Examples PDF]
(No email required. Just print, post, and protect.)
Need Help Making Your Team Scam-Proof?
At Arakyta, we specialize in helping small and midsize businesses protect what they’ve built. If your current IT plan doesn’t include regular awareness training and phishing tests, that’s a gap we can close—fast.
➡️ [Schedule a Free Consult]
Let’s make sure your tech, your team, and your future are secure.
FAQs: Phishing Edition
Q: How often should we train employees on phishing?
A: At least quarterly. Repetition builds habits and sharpens instincts.
Q: What’s a phishing simulation?
A: It’s a safe test where fake phishing emails are sent to your team to see who clicks and who reports.
Q: What if an employee clicks a phishing link?
A: Act fast! Disconnect the device from the network, report it, and scan for malware.
Q: Are smaller businesses really targeted that much?
A: Absolutely. Hackers know that small businesses often lack robust security and training.
Final Thoughts: Stay Sharp, Stay Safe
Cybercriminals are getting smarter, but your team can too. By showing employees real phishing examples, teaching them red flags, and offering simple, ongoing training, you’re building a stronger front line against attacks.
Remember, you don’t need to be a cybersecurity expert to protect your business—you just need to be proactive.
🎯 [Grab the Free Guide] and get your team phish-proof, starting today.